The Central Information Technology Office (CITO) would like to inform the public, and computer users in general, to be on the lookout for ransomware called Wannacry. So far, computer networks in over 150 countries have been impacted by the ransomware which takes over users’ files, demanding cash payments to restore them.
We are pleased to report that no government systems have been affected by this malware since its detection last Friday, May 12th.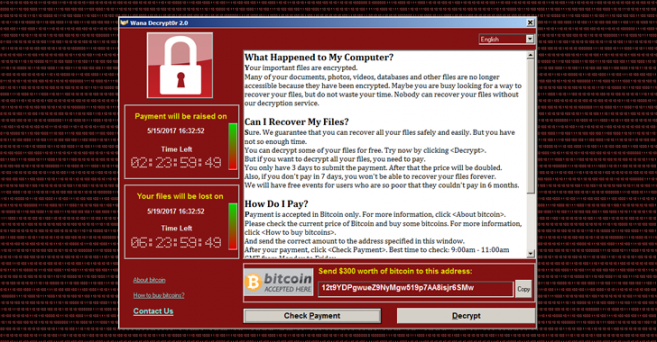
Users of the Government’s computer networks managed by CITO benefit from security measures that safeguard our critical systems and protect them from malware intrusions such as these. The Central Information Technology Office uses a firewall to scan incoming traffic for any application that may intend to do harm to the network as the first line of defense. The Windows firewall installed on each workstation is also turned on to protect those machines from being infected.
CITO also takes extra measures to secure the Government’s network by enforcing a policy whereby a user has to register external storage devices such as universal serial bus (USB) drives. Such devices are scanned each time they are inserted or removed from a machine. Along with these policies, CITO also uses advanced antivirus protection to prevent their users, and by extension the Government, from falling victim to these malicious attacks.
As a means of lessening attacks, regular windows updates are enforced on all machines. That is to say, users of machines on the Government network do not dictate when and whether a windows update can run – these are run automatically; thus, the patch for the Wannacry malware was automatically applied to all machines on the network.
In addition to this, vulnerability scans, using advanced tools, are done on a regular basis to detect any weaknesses within applications and systems operating on the network. If any are found, they are addressed within a specified time period as per policy. All emails received by machines on the network are also scanned for viruses and other malware.
The Government network is also safeguarded by high-end routers and switches that allow CITO to lock off any doors that may be left open, and a password change is required every three months for all machines. Further to this, hourly backups are in effect for all data and all servers on the Government network.
With all these measures in place as standard operating protocol, we were able to circumvent the Wannacry ransomware from causing any harm to the Government of Belize. Users are encouraged to contact CITO if they see any suspicious email messages or attachments.
The public can take precaution in purchasing well-known antivirus software or using free software such as AVAST, which work really well. Use antimalware software such as Malwarebytes to periodically scan your machines. Most importantly, install Windows updates to ensure your machines are well protected and up to date. If you do fall victim to a severe malware attack that your regular antivirus cannot handle, your best recourse is to seek help from an IT specialist and have your machine reformatted and important files scanned and backed up.
Share
Read more

